BOOK RELEASEd - OCT 2022
Implement Zero Trust initiatives efficiently and effectively
In Project Zero Trust: A Story About a Strategy for Aligning Security and the Business, George Finney, Chief Security Officer at Southern Methodist University and our founder, delivers an insightful and practical discussion of Zero Trust implementation. Presented in the form of a fictional narrative involving a breach at a company, the book tracks the actions of the company’s new IT Security Director.
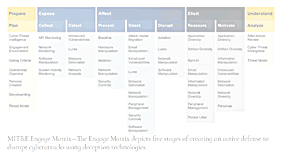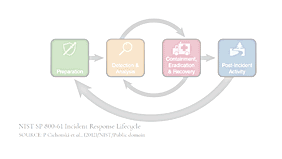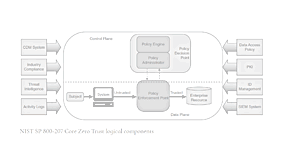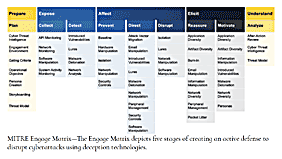
- Readers will learn John Kindervag's 5-Step methodology for implementing Zero Trust, the four Zero Trust design principles, and how to limit the impact of a breach.
- Project Zero Trust is an ideal resource for aspiring technology professionals, as well as experienced IT leaders, network engineers, system admins, and project managers who are interested in or expected to implement zero trust initiatives.
DOWNLOAD THE AUDIO COMPANION GUIDE ABSOLUTELY FREE
TRY OUT CHAPTER one TOTALLY FREE
"Well Aware shows you don’t need a degree in computer science to safeguard your community. George Finney’s nine cybersecurity habits make protecting yourself online approachable for anyone.”
—Daniel H. Pink, New York Times Bestselling author of When, Drive, and To Sell Is Human
“George Finney has written a must-read primer for anyone who wants to protect themselves online . . . particularly for leaders who need to protect their organizations. With this book, you can learn from one of the best.”
—Robert Glazer, best-selling author of Elevate, Friday Forward, and Performance Partnerships
“George has documented an incredibly practical and holistic overview of the foundational elements of cybersecurity practice and business in general. Definitely worth the read.”
— Stuart McClure, former CEO of Cylance and author of Hacking Exposed






George Finney.
CEO & founder
Subscribe to
Whether you’re a business or HR leader who is looking for non-technical ways to contribute to company cybersecurity or a professional with organizational influence who is looking to understand technology to avoid future issues at work and the whack-a-mole approach to securing your personal devices, Well Aware Security is here to provide answers.
cyber security Digest
Receive timely and tactical cybersecurity habits delivered to your inbox.



