Have you ever been told to never write your password down? Or never use social media? Don’t click on links? Never use Wi-Fi at a coffee shop? Cybersecurity should be easy, but sometimes advice like this makes it seem hard. We think making cybersecurity can be easy, you just need to build habits.
There are a lot of good tips out there on how to be more secure. But this advice is missing a key ingredient. The most important part of the recipe to good security isn’t the advice itself, it’s how to incorporate that advice into your life the way you live it. The reason that most generic advice doesn’t work isn’t because it’s bad. It doesn’t work because it asks you to do the hardest part on your own. You have to figure out how to take the advice and incorporate it into your life the way you live it.
It can feel like security can be a lot of extra work that we just don’t have time for, but what if instead it was easy?
We think that improving our security starts with building habits. Habits make up 40-50% of our daily lives. We don’t think about them; they don’t take any extra time or feelings of effort, because our brains push habits out of our conscious mind. And when you’re successful with a building a habit, it’s because you’ve figured out the secret recipe to making a behavior fit your life and who you are as a parson.
Stanford Professor BJ Fogg is one of the country’s foremost experts on behavioral design and is the author of the book, Tiny Habits. In the book, he says that every habit has a repeatable loop with three important parts: the cue or prompt, the behavior or routine you want to create, and the celebration or reward at the end.
Every behavior you exhibit is initiated by some prompt, and by recognizing those prompts you can begin to initiate new behaviors or to stack new behaviors on top of existing ones. The reward or celebration is just as important because they send signals to your brain that you will want to repeat this behavior in the future, cementing the new routine.
And to create these habits, you’ll be most successful if you start small…no, that’s too big…start smaller than that…think tiny. Starting tiny will ensure that you’re successful from the beginning, which will translate in you having the willpower to stick with the new habit long enough for the habit to be established in your brain.
Recipes for Success
To find success in building habits, we need to start with a recipe that involves all three ingredients, prompts, behaviors, and celebrations. To get started, we’ve provide a list of sample prompts and rewards that might work for you. As you look through the list, think about which would pair best with the security behavior you’re wanting to create or improve. And which reward might make the most sense in that situation.
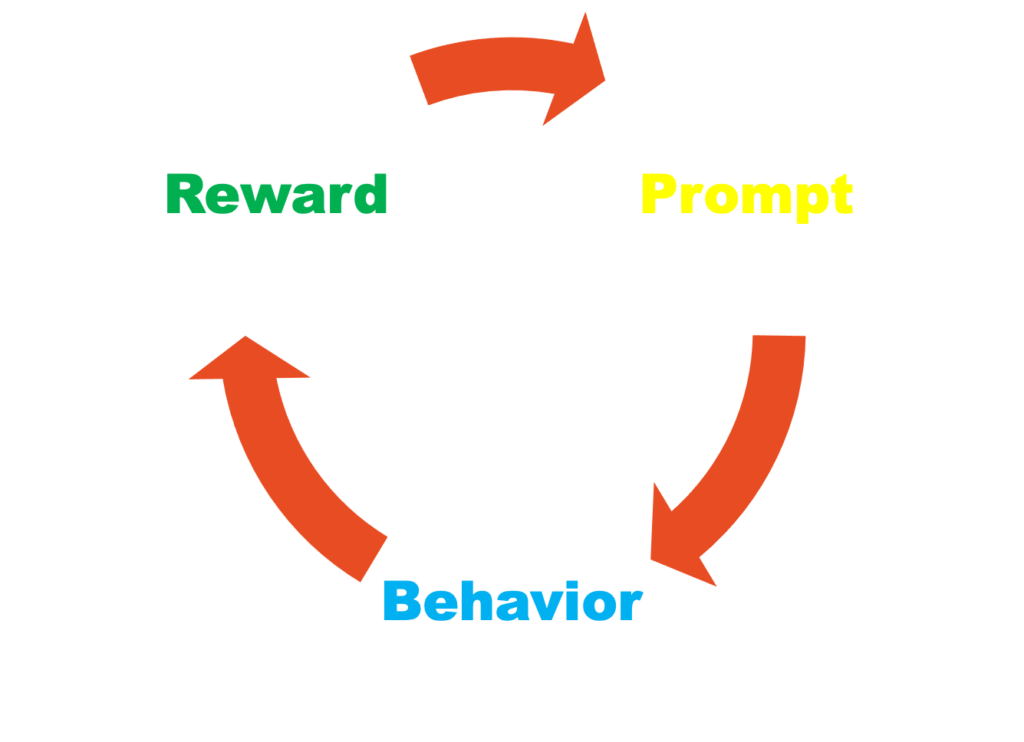
The example we like to use is locking your computer before you leave your desk. Breaking this advice down into a habit recipe, you’ll need to identify a prompt and a celebration. For me, the prompt is the action of pushing my chair away from my desk. I find that I press the ctrl-alt-delete key combination as I’m standing up. And as my reward, I might play a little air guitar to celebrate my tiny cybersecurity victory for the day.
Locking your computer is a great habit to start with because it’s tiny…just press ctrl-alt-delete and hit enter and you’re done. But once you build this habit it will start to change you into a security superhero. Your identity will start to change you into the kind of person that loves security and you’ll find yourself starting to think about changing other cybersecurity behaviors like securing your passwords.

Another habit recipe that you can start with is a technique I call “Slow Down and Frownâ€. The “Slow Down and Frown†habit recipe might look like this:

We tested this technique during SMU’s Biggest Phisher contest held during the month of October. We secretly separated the participants into two groups, and taught the experiment group the “Slow Down and Frown†technique. At the end of the tournament, the frowners were 43% less likely to have clicked on a phishing message than their non-frowning counterparts. But there was another unexpected benefit…the frowners were also nearly 3 times more likely to report the phishing messages to the help desk.
There are nine different “constellations†of habits that I identify in my book, Well Aware. To improve our cybersecurity, we should identify what our own strengths and weakness are in each of the nine cybersecurity habits and then decide which habits we want to focus on. And keep in mind that the habits we pick first should be simple like the two examples above in order to built up momentum for tacking the bigger things we want to accomplish.
If you’ve been meaning to start using a password manager, here’s a sample recipe for that:

Being cybersecure can feel like it’s too technical and would be too much work to actually accomplish. Habits are your secret recipe for success this year when it comes to changing your cybersecurity for the better. The other advantage that habits provide is that when we’re following our habits, our reaction times are much faster than if we had to stop and think about what to do.





2 Responses